Monitoring and control
Job Logging in i-effect
The individuals processing steps of commands in use can be recorded and followed in the i-effect Logbook. Every registered command (or a command chain using *SERVER) has its own session number under which all logging entries are saved within the logbook.
Use the Function Key F13 to reach the logbook from the i-effect menu.
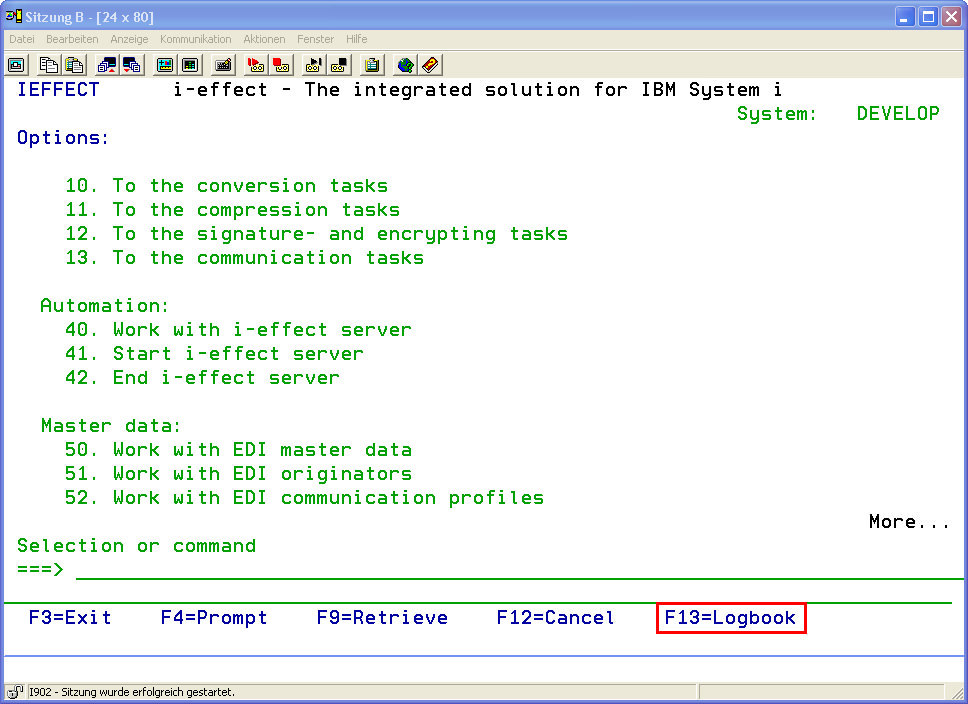
The first page of the logbook will be displayed. Using the PAGE-UP or PAGE-DOWN - keys will page through the logbook.
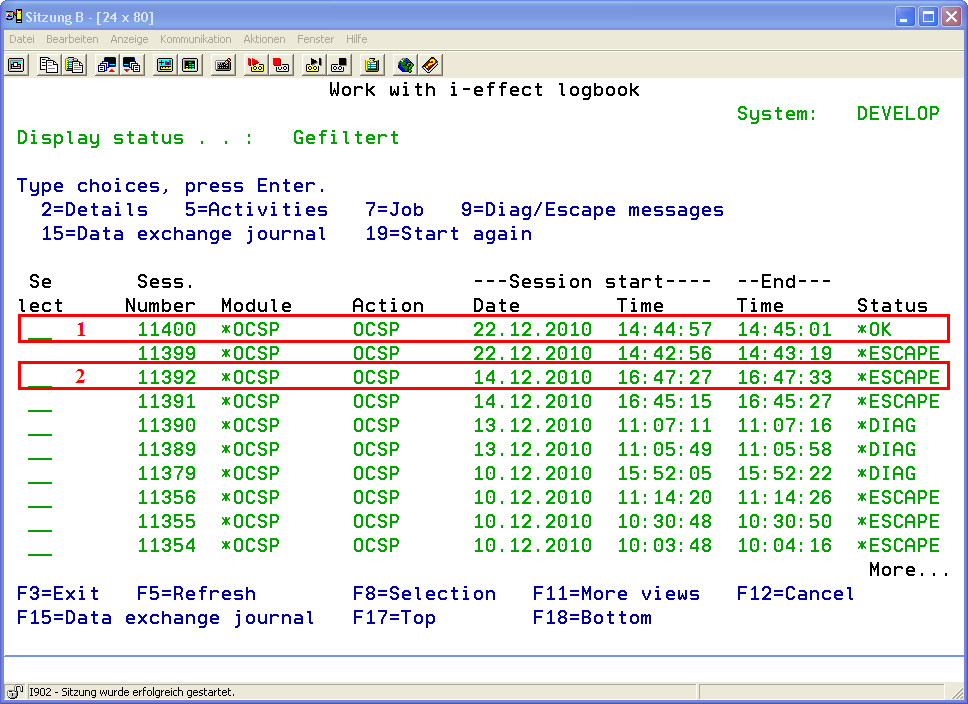
In the status column of the logbook, the current processing status or the status in which the command ended can be seen.
With *OCSP, verification can basically only be ended with a correct (1) or an error (2) result.
To display the details of a finished verification job, move the cursor by using the arrow keys to the desired entry. Enter Option 5 and press enter to reach the detail view (Here *OK):
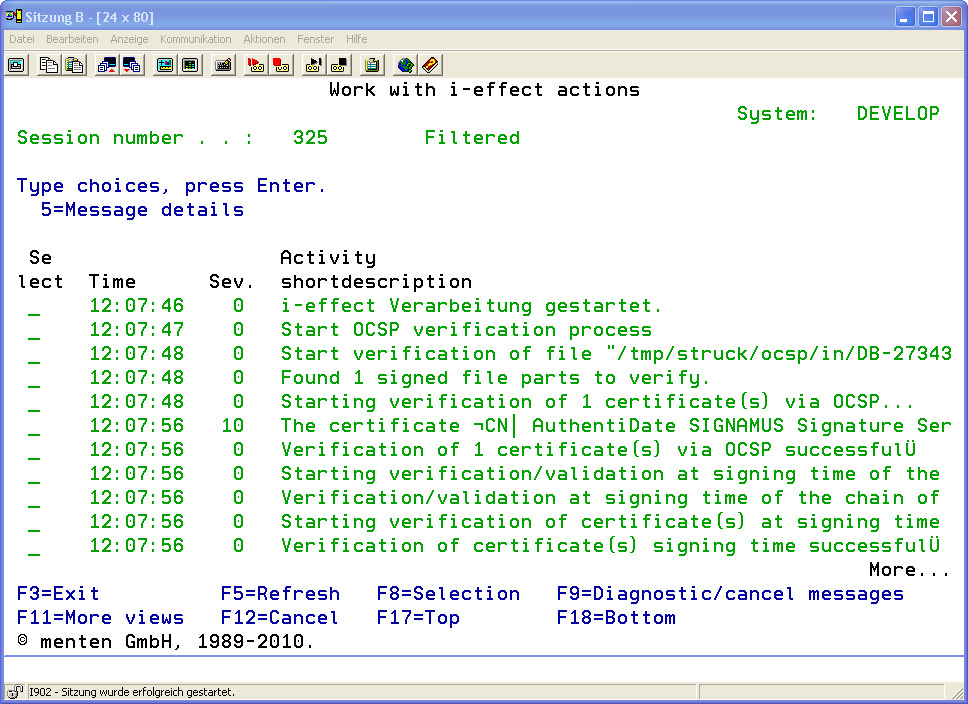
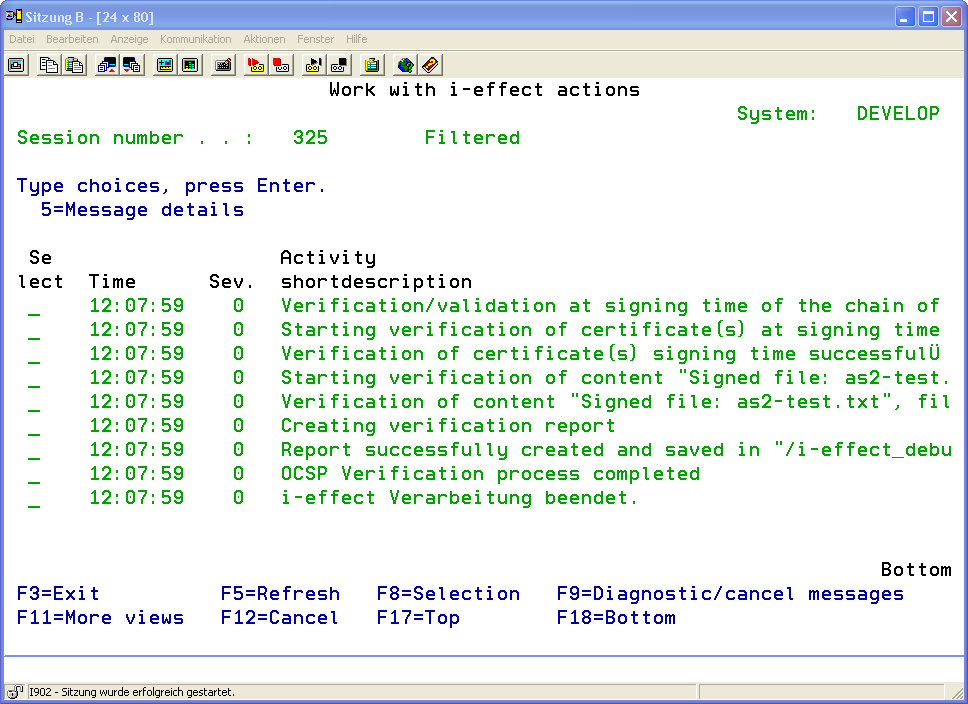
The detail view displays over two pages of processing steps that the verification job gener-ated. Using Option 5 will display the individual processing steps completely.
The report of a successful verification lists the details in the area called "Test Results" of the results of the individual processing steps:

If an error occurred at least one of the steps will have an error status:
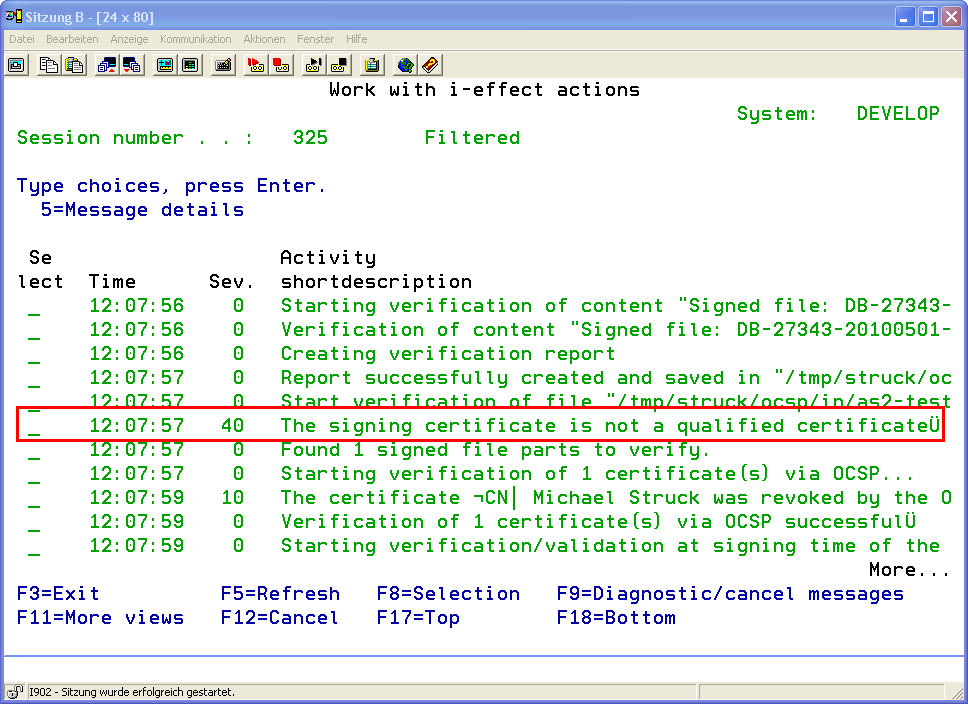
With a message severity of 40, the error status and the text description will be displayed and the entire processing will be set to *ABORT.
In the case displayed here, the certificate could not be verified by OCSP. In this case, the processing will not be stopped, but rather verification of the signed file will be continued.

The result created a test report that is displayed in the "Test Result" area, and contains a detailed list of which processing steps were completed successfully and which were not.

In this example of a failed test, the verification of the signed data shows a manipulation of the original document.
*DIAGNOSE is an additional status, in conjunction with test report creation.
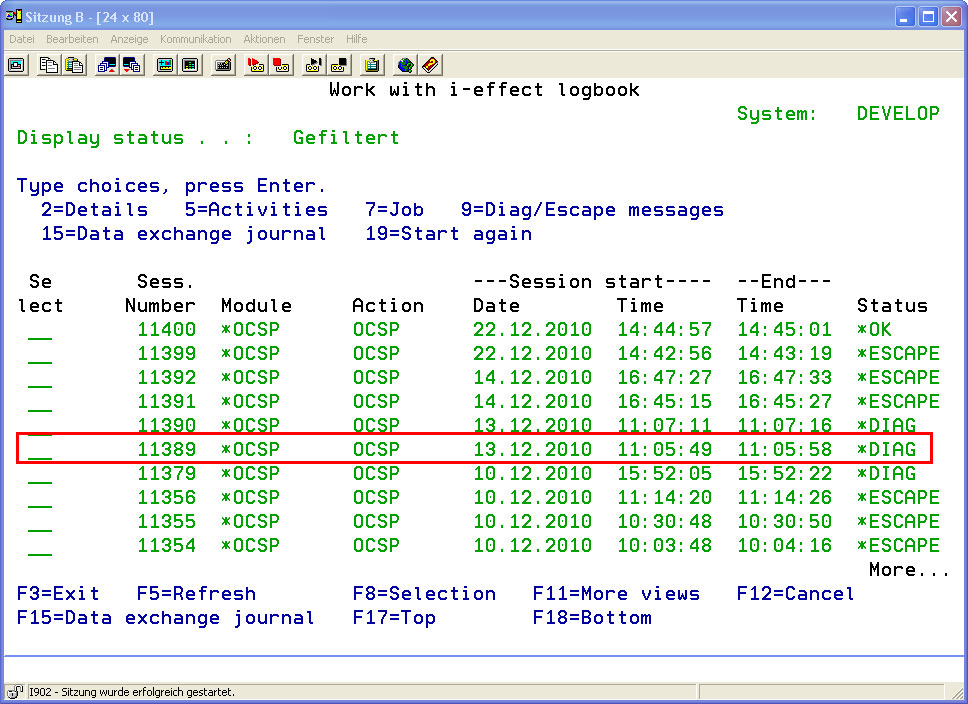
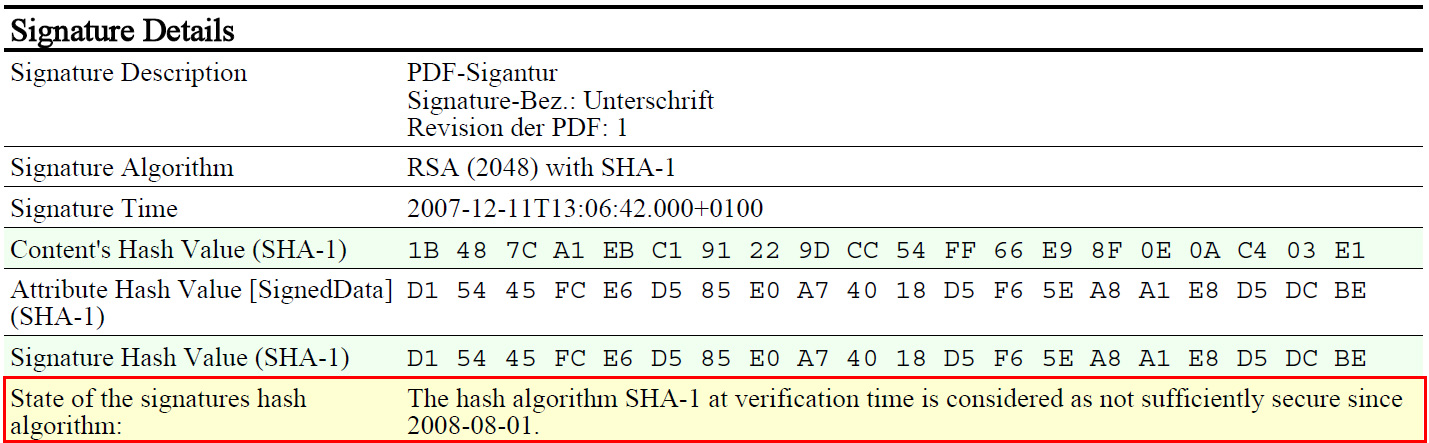
*DIAGNOSE generally means that verification was successfully completed. However, verification indicated, that either the hash-algorithm or the RSA key length (or both) are (were) no longer adequately secure at the time of verification (more information can be found at the German Federal Network Agency's website).
The report will also contain a marker regarding the algorithm verification status:
Logging in the 'internal'-Directory of i-effect
In the „internal"-directory of an i-effect-Installation detailed information regarding the processes of individual i-effect modules are logged, which helps find and correct possible problems.
The log file for the *OCSP module will be generated using the pattern "yearmonthday-ocsp.log".
This logging is an expansion of the i-effect logbook and records further information that was generated by the i-effect *OCSP-Subsystem.
