Introduction
The i-effect command STRPGP works according to the OpenPGP standard (RFC 4880) to encode and decode signing and verification of data. It can be used to sign, encode and decode any files compatible to the OpenPGP.
Key rings
To be able to work with STRPGP, you need a keypair. Your communication partners can use the public part of the key to encrypt data sent to you and you can use the private part to sign data sent to others.
PGP keys can be produced with the free available Windows Program Gpg4win (URL http://www.gpg4win.org/index.html).
The Gpg4win installation package includes the graphic tool Kleopatra, with which PGP key rings and keys can be administered.
Install Gpg4win on your PC and start Kleopatra.
Create a private/public key pair
Click on the button New Key Pair to start creating a new private/public key pair
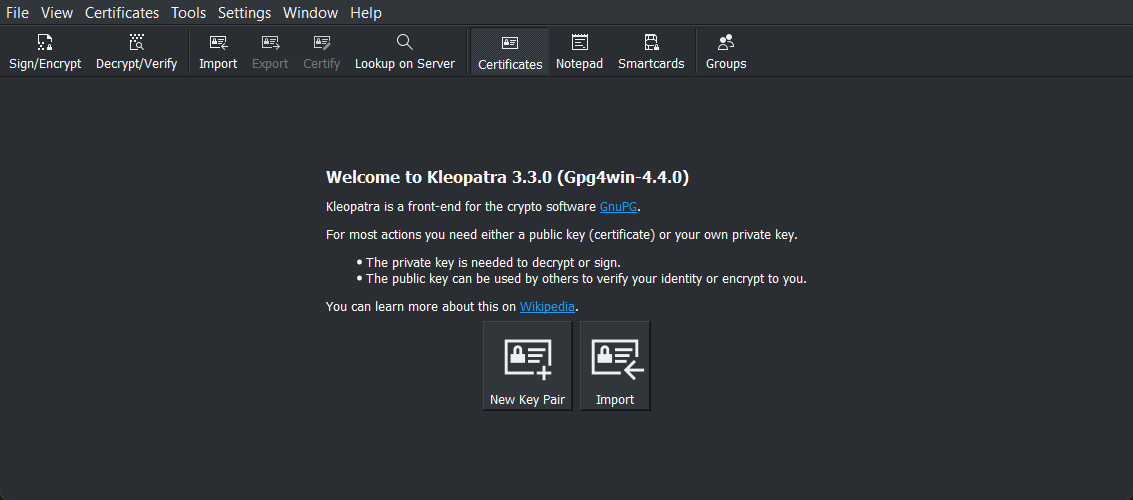
Kleopatra start page
Fill in the following fields with your personal information:
Name - A unique Name for the keypair entry to be created
Email address - An E-Mail address to be used with this entry
It is recommended to check the box Protect the generated key with a passphrase
Key Material - Select one of the rsa keys: rsa4096 or rsa3072 or rsa2048
Klick OK, after entering the above data.
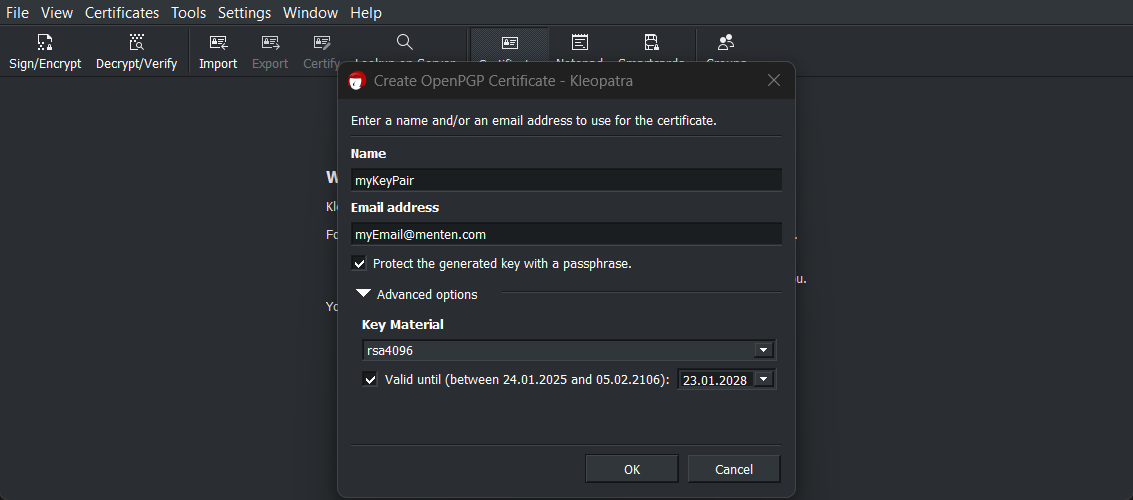
Key Pair details
Enter a passphrase to protect your key pair:
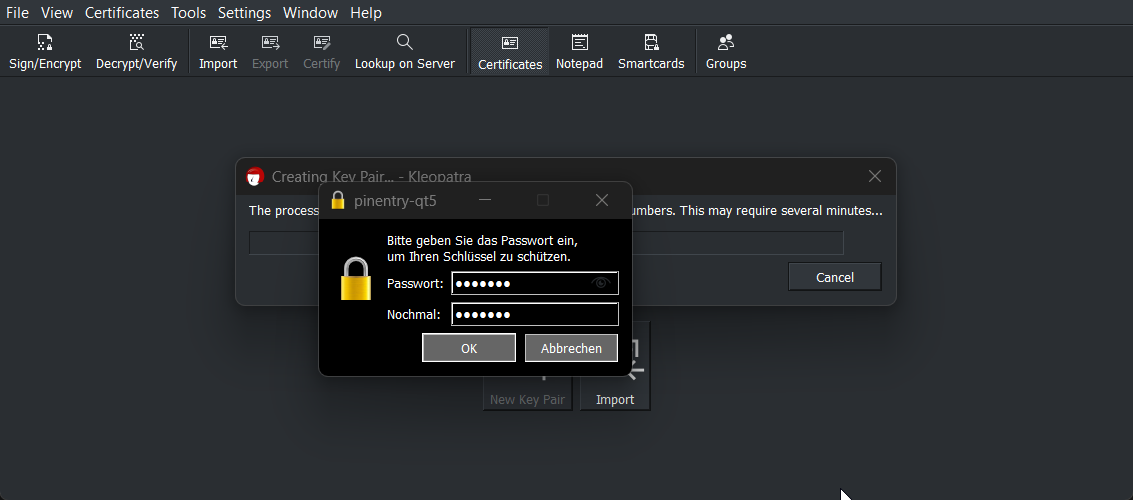
Passphrase to protect the key pair
Press OK to start the key generation.
Find the key ID
Double click the generated entry to open the following information details view.
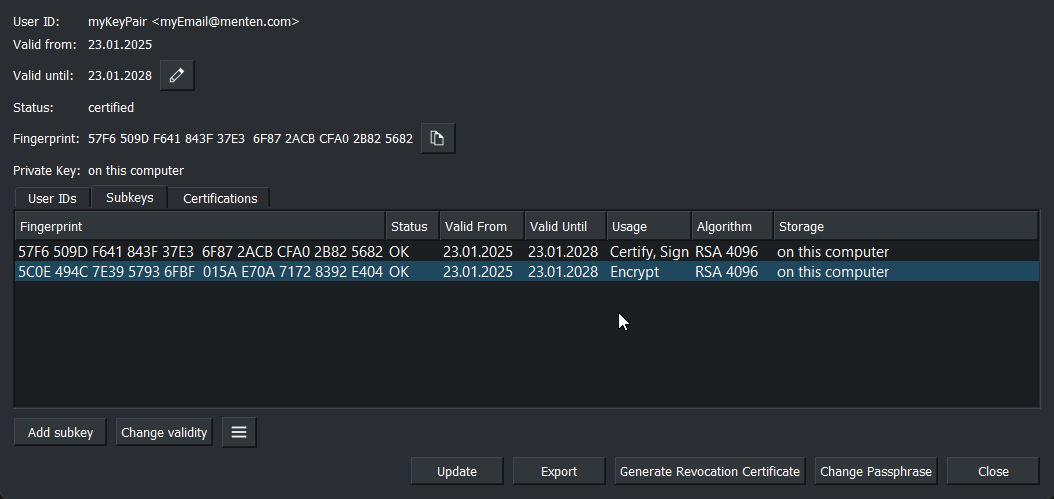
Details for the generated keys
Write down the 8 rightmost bytes of the Fingerprint of the entry having Encrypt in column Usage. In this example this is:
8392E404Export the private and public key
Start a Terminal and enter the following commands. Replace the 8 bytes fingerprint in this example with your id that was identified in the previous step.
gpg --output pubring.gpg --armor --export 8392E404
gpg --output secring.gpg --armor --export-secret-key 8392E404Copy the exported keys to i-effect
Copy the created files pubring.gpg and secring.gpg into the i-effect CRYPT directory of the IBM i system (/home/ieffect/crypt)
