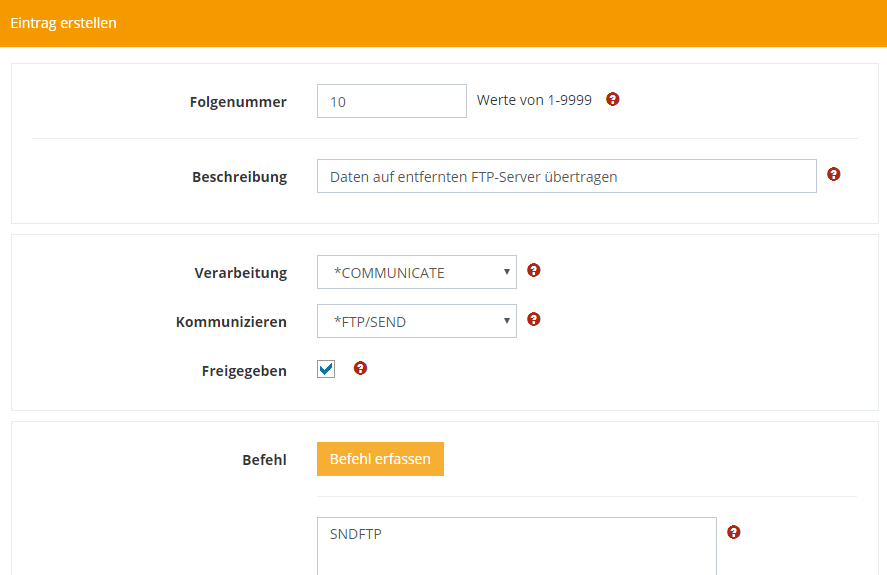
Send data with FTP (SNDFTP)
The SNDFTP command is used to send any data via FTP using predefined partner or communication profiles.
When transferring objects from DB2 ( FS(*DB2) ) to another IBM Power Systems System ( TARGETPATH(*FRMPATH) or TARGETPATH(/qsys.lib/...) i-effect uses the standard commands SAVOBJ and RSTOBJ. The standard parameters used for these commands are defined in the message file NACHRICHT. Should it be necessary to specify special parameters for this in your environment, the following messages can be adapted:
IEF0066 Template for the RSTOBJ command
IEF0067 Template for the SAVOBJ command
To transfer data to an FTP server, choose *COMMUNICATE during processing and *FTP/SEND during communication..
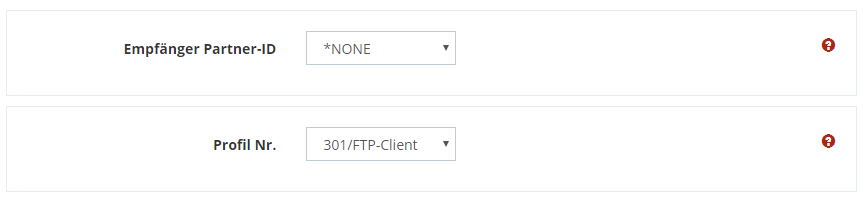
Now choose whether you want to use a partner or communication profile as the receiver.
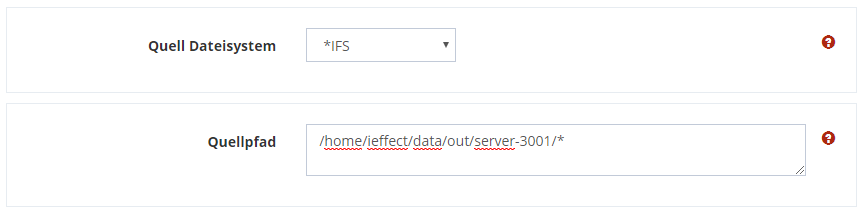
Select the file system from which you want to send.
Select *IFS as the source file system and enter the path to the files you want to send to.
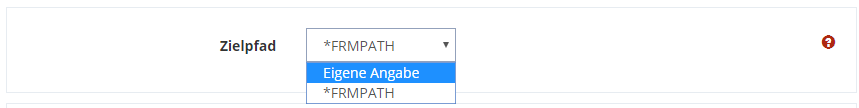
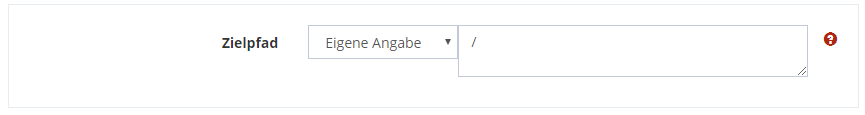
Then enter the destination path on the remote FTP server. You can use the value *FRMPATH if the file is in the same location as in the source system.
However, this is often not the case, so you enter your own path here, e.g. the home directory,
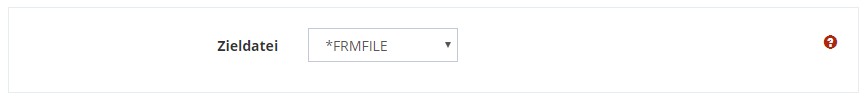
Similar to the path specification before, you have the option of copying the file name of the source file (*FRMFILE) or assigning your own name.
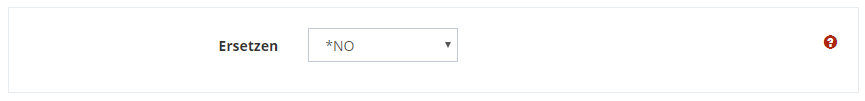
You must also specify whether the file should be overwritten, if it already exists.
If you want to execute your own commands on the remote server, specify the command and the execution time. You can choose between *BEFORE (Before transmission) and *AFTER (After successful transmission).
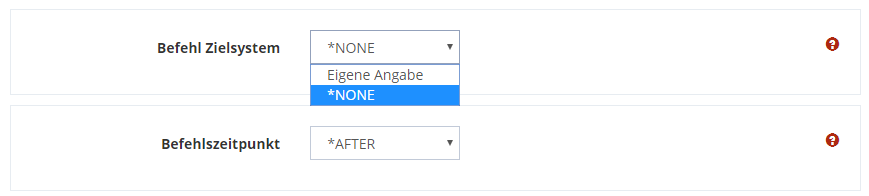
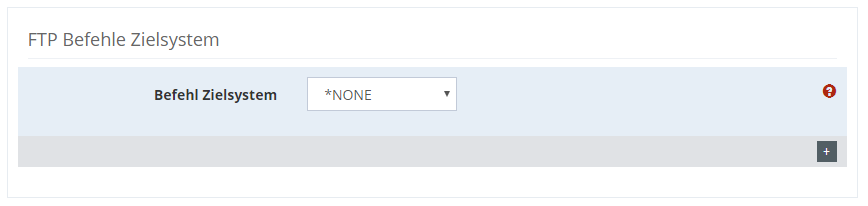
You can also execute several commands in succession.
To rename the files after successful transfer (if necessary at all) the following parameter is suitable.
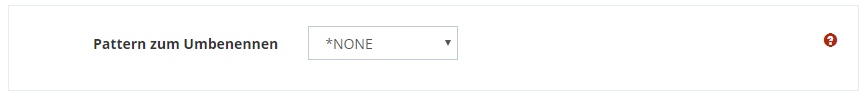
*.DONE // Aus "file1.txt" wird "file1.DONE"
*_DONE.* // Aus "file1.txt" wird "file1_DONE.txt"
*_1055am // Aus "file1.txt" wird "file1.txt_1055am"Finally, decide whether the source file should be deleted after successful transfer.
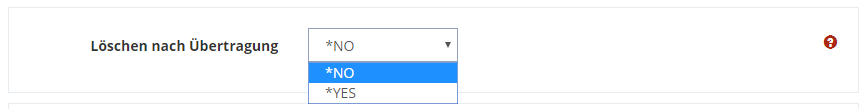
If necessary, you can still choose one of the following encryption methods.